CLZero: A project for fuzzing HTTP/1.1 CL.0 Request Smuggling Attack Vectors
Fuzzing with CLZero is a dedicated project designed for testing and identifying vulnerabilities in HTTP/1.1 CL.0 Request Smuggling Attack Vectors. This tool focuses on systematically probing and analyzing potential weaknesses, offering a valuable resource for enhancing the security of web applications.
Usage
usage: clzero.py [-h] [-url URL] [-file FILE] [-index INDEX] [-verbose] [-no-color] [-resume] [-skipread] [-quiet] [-lb] [-config CONFIG] [-method METHOD]
CLZero by Moopinger
optional arguments:
-h, --help show this help message and exit
-url URL (-u), Single target URL.
-file FILE (-f), Files containing multiple targets.
-index INDEX (-i), Index start point when using a file list. Default is first line.
-verbose (-v), Enable verbose output.
-no-color Disable colors in HTTP Status
-resume Resume scan from last index place.
-skipread Skip the read response on smuggle requests, recommended. This will save a lot of time between requests. Ideal for targets with standard HTTP traffic.
-quiet (-q), Disable output. Only successful payloads will be written to ./payloads/
-lb Last byte sync method for least request latency. Due to the nature of the request, it cannot guarantee that the smuggle request will be processed first. Ideal for targets with a high
amount of traffic, and you do not mind sending multiple requests.
-config CONFIG (-c) Config file to load, see ./configs/ to create custom payloads
-method METHOD (-m) Method to use when sending the smuggle request. Default: POST
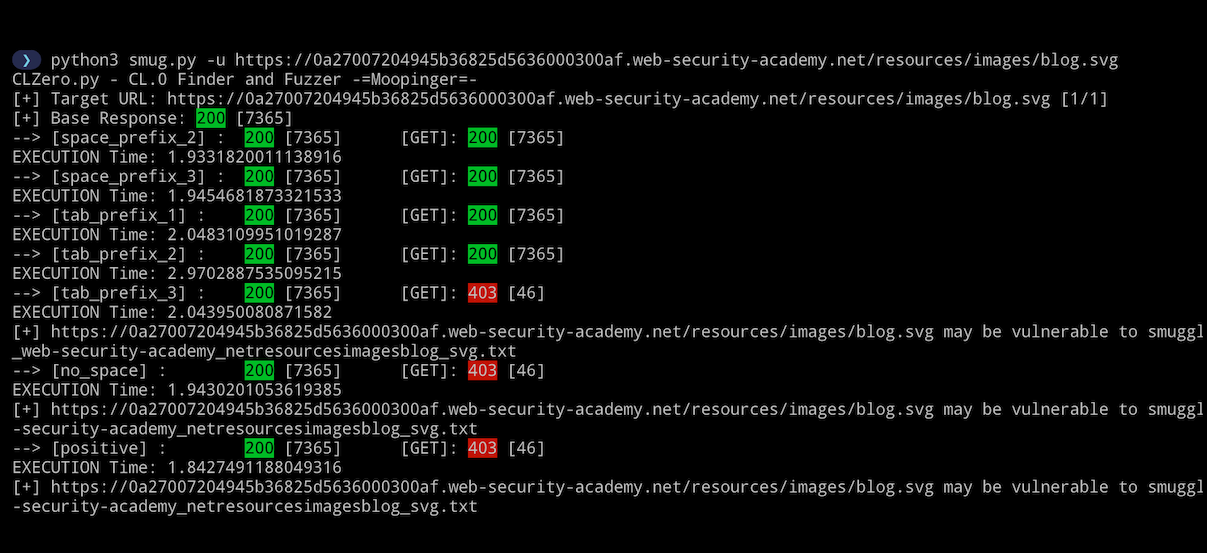
Regular (smug.py is clzero.py with some debugging enabled):
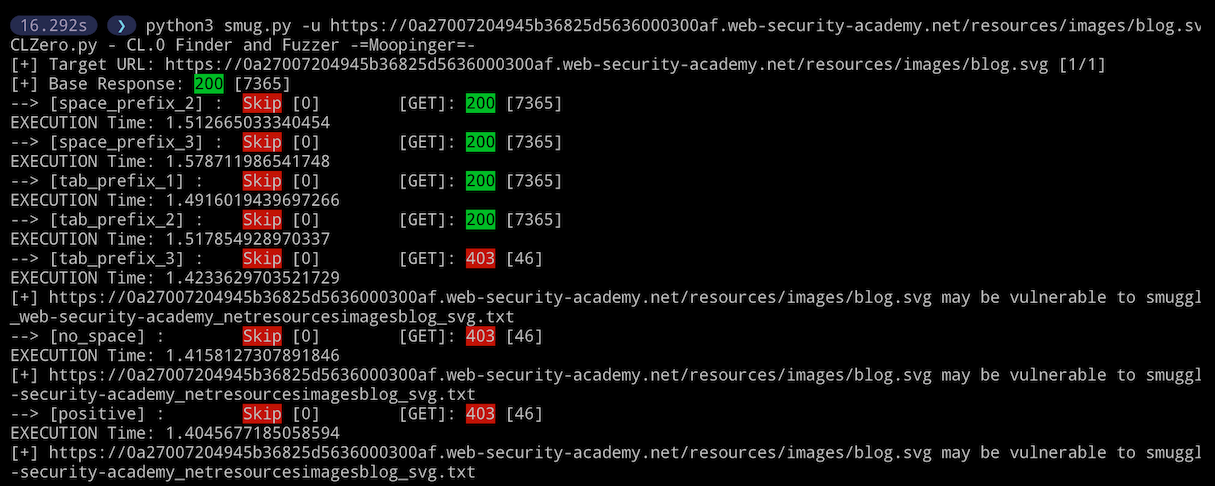
Skipping read on the Smuggle request ensures less time between requests:
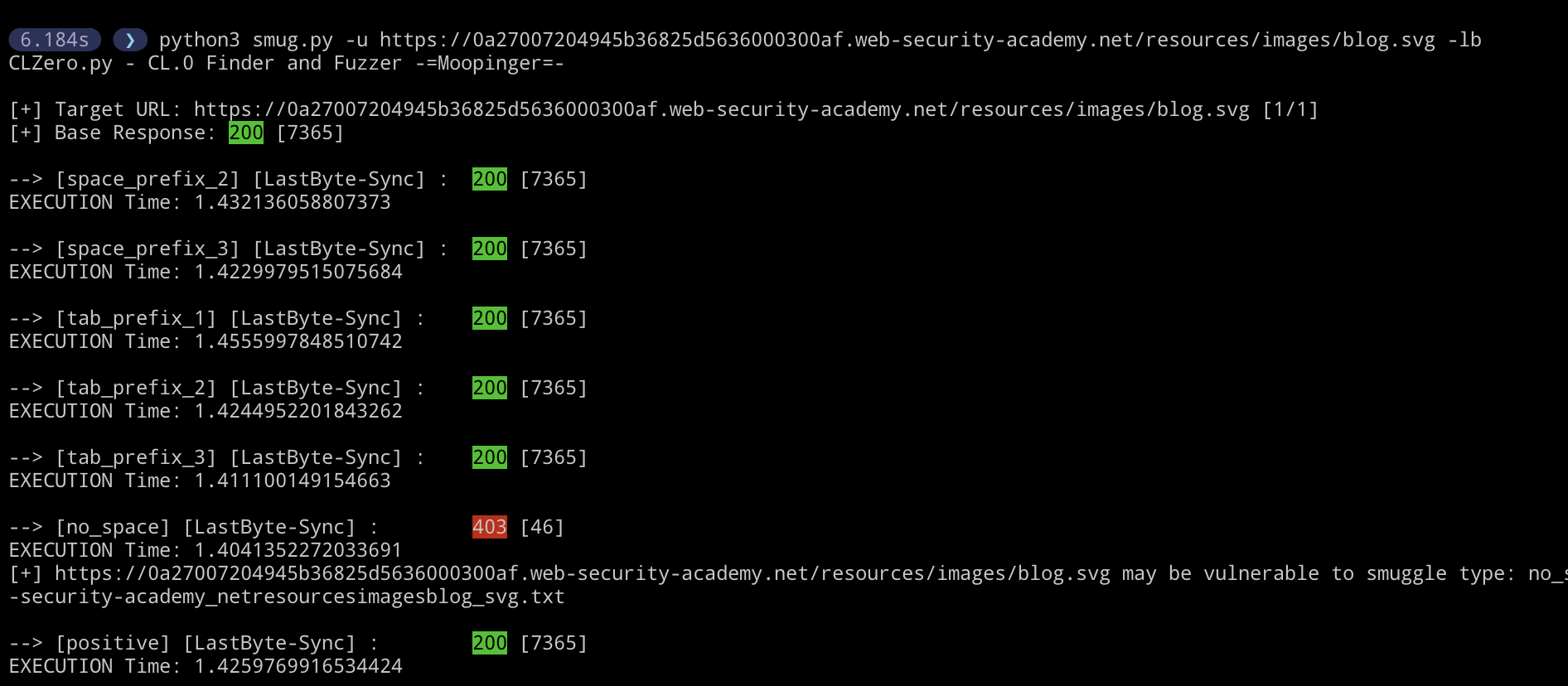

More Speed with last-byte sync
What’s that… you need more speed? “She’s at max captain!” Just kidding. If the website has high amounts of traffic this will be your best bet. I have adapted the HTTP/1.1 last-byte sync race condition (No, not the cool one you heard about at Defcon this year, that requires HTTP/2). This saves even more time between the smuggle request and probe. However, there is a catch… We cannot guarantee which will be processed first by the server (The smuggle-gadget or the probe). Such is the nature of race conditions I guess. However if you don’t mind testing the same technique more than once on a high traffic site, this will be your best bet. And it should trigger within two or three requests. Strangely I have had better success with this than the skip-read technique.
single target attack:
python3 clzero.py -u https://www.target.com/ -c configs/default.py -skipreadpython3 clzero.py -u https://www.target.com/ -c configs/default.py -lb
Multi target attack:
python3 clzero.py -l urls.txt -c configs/default.py -skipreadpython3 clzero.py -l urls.txt -c configs/default.py -lb
Install
git clone https://github.com/Moopinger/CLZero.git
cd CLZero
pip3 install -r requirements.txt








